Benefits and challenges of enterprise AI in the banking and finance sector
See for yourself how enterprise AI transforms banking and finance. Learn about its benefits, challenges, and strategies for successful adoption.
Digital security is a goal that unites business partners on both sides – the IT service provider and the customer. It is high time we forget the approach of defending one side of the barricade or the other. Companies globally invest more and more in portals and platforms for secure data exchange, and not only in those areas related to operational cooperation. Organizations are also interested in the cross-integration of services to automatically and securely exchange their data. So, the future lies in platforms and channels that enable secure communication between multiple business partners, and the real key to success will be the speed and ease of implementation.
Imagine that you live on the outskirts of town, you have a beautiful house surrounded with a high fence, and you have video surveillance and a pit bull. You’ve taken care of your security as best you can. You also have a neighbour whom you have known for years and who enjoys your trust. Only a wooden fence and a small gate separate you from their property. There are some unwritten rules of conduct and boundaries are set.
One day a lawn mower disappears from your yard. The surveillance video clearly shows that the thief got through an unsecured gate on your neighbour’s property. On the one hand you know that your neighbour is not the thief, but on the other hand you blame them for not taking proper care of the security for their property. You blame others, but not yourself. After all, you did everything to prevent this from happening. But, are you sure about that?
The problem described above is not new, but it is difficult to be solved despite its simple appearance, especially on a business level. Areas such as business needs, security, and legal requirements overlap where the world of contracts and the world of people’s actual activities often diverge.
One way to minimize these discrepancies is through interfaces, applications, and platforms that enable the secure collaboration between business partners. We can already see this in the B2C sector, especially in e-commerce solutions. It will also dominate the B2B space, where One Trust and similar products will become the standard in the coming years.
Are companies (un)safe?
According to the 2020 State of Security Operations report published by Forrester Consulting (02.2020), as many as 47% of all companies have had a security problem in the last 6 months.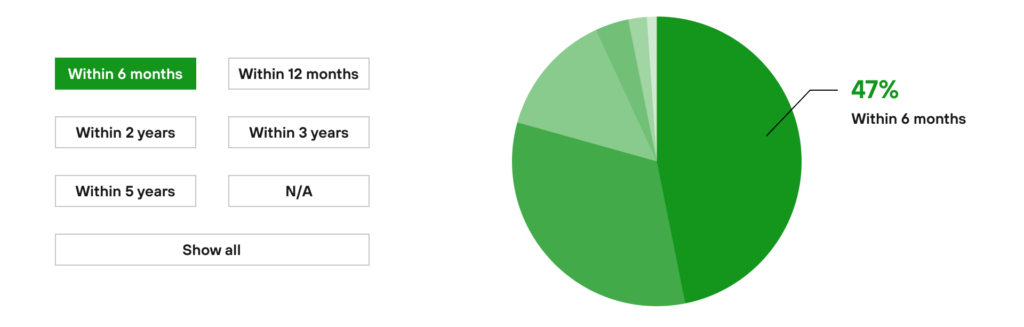
Source: a proprietary compilation based on: https://www.paloaltonetworks.com/resources/infographics/cortex-forrester-2020.html
The study also shows that the biggest challenge for company security teams worldwide is the increasing pace, volume and complexity of cyber-attacks, which have escalated even more during the pandemic period.
→ Read more about Security challenges in cloud native architectures
This is confirmed by Tonya Ugoretz, Deputy Director of the FBI’s Cyber Security Division, who said that the IC3 (Crime Complaint Center) receives an average of 3,000 to 4,000 cybersecurity complaints every day, compared to about 1,000 in the time leading up to COVID-19.
Meanwhile, Gartner, in its October 2020 reports, points not only to an increase in reports of business email intrusions, but also to a growing number of phishing scams, including SMS phishing (smishing) as well as credential thefts.
The spike in attacks is affecting those companies and industries whose security levels are far from perfect, as evidenced by Forrester Consulting’s findings, among others.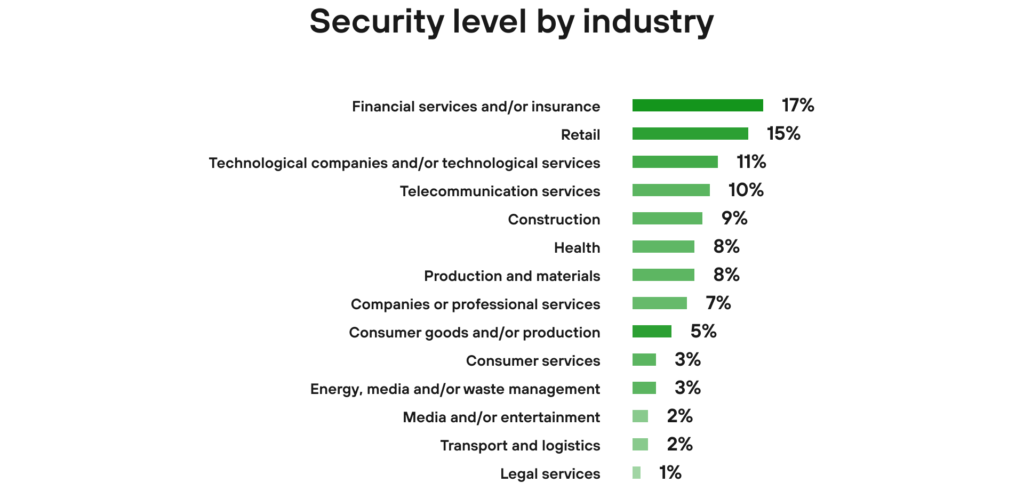 Source: a proprietary compilation based on:
Source: a proprietary compilation based on:
https://www.paloaltonetworks.com/resources/infographics/cortex-forrester-2020.html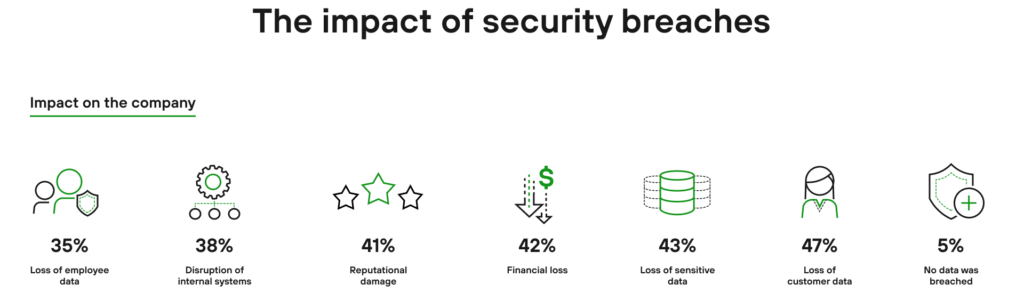
Due to the increasing scale of attacks, the “Zero Trust” concept should become the strategy of any company that wants to safely grow their business.
The Zero Trust concept focuses on the idea that organizations should not trust anything inside or outside their operations, and instead, they must vet everything that tries to connect to their systems. It is a way of thinking about security that uses such solutions as:
As with other IT activities today, Zero Trust is not just about technology, it’s all about a mindset and a continuous improvement process.
→ Explore Zero Trust Architecture (ZTA) for more secure digital experiences
At Avenga, we believe this is the best basis for creating a well-thought-out strategy to guarantee a company’s digital security.
No one has a patent for security. Every company, no matter the size, wants to grow its business safety. It does not depend on the brand’s size and its recognition, but on conscious actions, which should be a part of every company’s strategy.
What does it mean to have a good plan? Our answer at Avenga is: be proactive. Proactivity is an attitude in which you take responsibility for what happens and don’t wait for someone to hand you a box of tools or for a situation to happen. As far as security is concerned, it is worth acting proactively and allocating proper data protection resources. The cost of data loss can be incommensurably higher, can include operational paralysis and a negative impact on the brand image.
→ Read more about data privacy
In the world of cybersecurity, the rules of the game change frequently. The winner is the one who can keep up with them. How do we do that?
Sometimes security concerns can slow down a business. But it can also support it and be an added value. The Introduce Security by Design approach is based on designing secure company processes and activities. It involves all departments and operational staff within a company.
→ Read more about DevSecOps – DevOps with security
It is essential to operate with rules, procedures and standards, because on the other side you have an adversary who has no rules and principles. Nevertheless, good practices such as respecting ISO/IEC standards, conducting regular audits, renewing certifications, and continuously monitoring and improving safety are a solid foundation for good quality products and services.
A significant portion of business correspondence is conducted via email. However, with today’s technological advances, there are many other solutions that are more convenient and secure. These include:
▪ Partner portals (e.g., Cisco, Shell, Unilever)
▪ Portals and dedicated network drives for customers (e.g., Warta, Allianz)
When you are using email correspondence, think about the security of the information you are sending. Use message encryption and send attachments with electronic signatures.
Communication in business is of paramount importance. Confidential information is often exchanged, so it is worth assessing whether the communication channels you are using are the most secure ones. Implement two-factor authentication, use one-time passwords, assign minimal privileges, and verify that basic security policies are in place. And, require the same from your business partners.
It takes trusted partners to defend against attacks and leaks of confidential data comprehensively. Procedures coupled with today’s technology, mean that company assets as well as working with customers and clients can be secure, provided we learn to defend our fortress beyond its doorstep.
* US and Canada, exceptions apply
Ready to innovate your business?
We are! Let’s kick-off our journey to success!