Addressing Key Data Pain Points In Achieving DORA Compliance

May 7, 2025 18 min read
Discussing the complexities of DORA compliance: key data challenges and strategic solutions.
In 2024, data breaches have cost businesses an average of $4.45 million, emphasizing the critical need for robust cybersecurity measures. As of January 17, 2025, the Digital Operational Resilience Act (DORA) will come into effect, creating a unified framework to ensure financial entities within the EU can withstand, respond to, and recover from all ICT-related disruptions and threats.
As financial institutions prepare for the January 2025 compliance deadline, they face numerous data-related challenges. These challenges span various domains, including ICT risk management, incident reporting, resilience testing, third-party risk management, and information sharing. Understanding and addressing these pain points is crucial for achieving compliance and safeguarding against emerging cyber threats.
This article explores the main data pain points in achieving DORA compliance. It also offers strategies to overcome them. These strategies ensure strong operational resilience in a more digital world.
Understanding DORA Compliance
DORA is a regulation established by the European supervisory authorities to enhance financial entities’ digital operational resilience. Its primary goal is to ensure these entities can effectively manage and mitigate risks associated with Information and Communication Technology (ICT) systems.
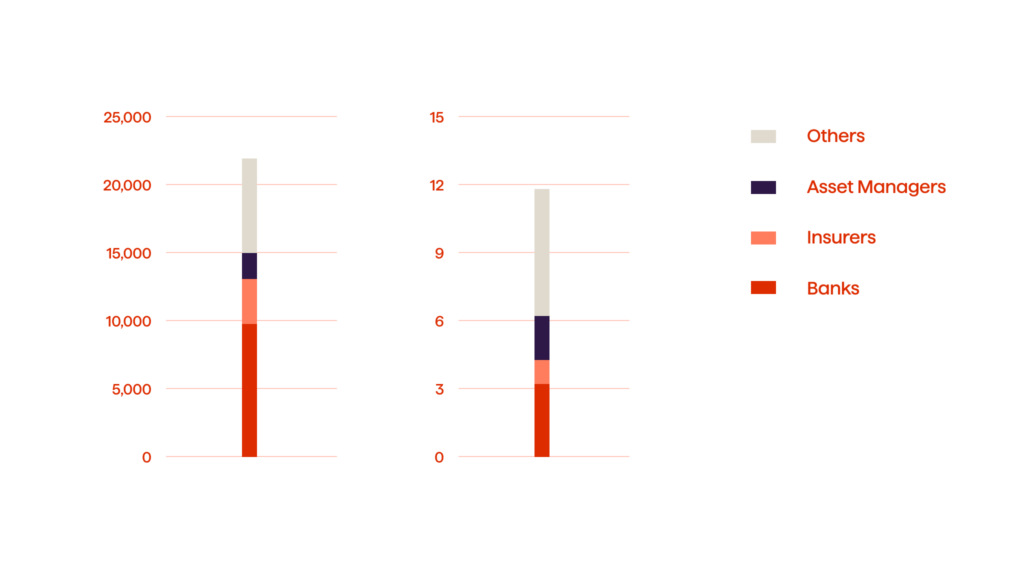
EU member states present DORA and set a comprehensive framework to safeguard financial institutions from ICT-related disruptions, including cyber-attacks, system failures, and data breaches. This is particularly important considering the financial sector suffered more than 20,000 cyberattacks totaling $12 billion in losses over the past two decades (see Fig. 1).
Scope And Applicability Across Financial Entities And ICT Service Providers
DORA requirements apply to various EU financial institutions and their critical ICT third-party service providers. These are the most important ones to mention:
- Credit institutions. Banks and other lending institutions
- Investment firms. Entities involved in securities trading and investment management
- Insurance and reinsurance companies. Providers of insurance policies and reinsurance services
- Payment service providers. Companies facilitating electronic payments and transactions
- Crypto-asset service providers. Firms offering services related to cryptocurrencies
- Management companies and AIF managers. Entities managing collective and alternative investment funds
- Third-party ICT service providers. Companies providing ICT services to financial entities, including cloud service providers and data centers
DORA aims to standardize ICT risk management across these diverse entities. It will ensure a consistent and strong approach to cyber resilience and digital finance.
Five Key Dora Pillars
DORA sets forth a unified framework designed to strengthen the digital operational resilience of financial institutions within the EU financial sector. This regulation mandates comprehensive measures across several key pillars, ensuring financial entities can effectively manage and mitigate ICT-related risks, enhancing their ability to withstand and recover from disruptions and prevent cyber risks.
I. ICT Risk Management Framework
Such an EU regulation like DORA mandates that financial institutions establish a comprehensive ICT risk management framework. This framework should cover all aspects of identifying, assessing, and mitigating ICT risks. The regulation requires entities to:
- Conduct regular risk assessments to identify potential threats and vulnerabilities.
- Implement security measures such as firewalls, encryption, and multi-factor authentication.
- Continuously monitor their ICT systems for signs of potential threats or breaches.
For example, a bank might deploy advanced intrusion detection systems to monitor for unauthorized access attempts and have protocols in place for immediate response and mitigation.
II. ICT Incident Management
Effective incident management is an aspect of DORA proposal that tries to make EU financial services as secure as possible. Financial entities must establish robust systems to detect, report, and respond to ICT-related incidents. This includes:
- Developing detailed incident response plans.
- Training staff on how to handle different types of ICT incidents.
- Reporting significant incidents to relevant authorities promptly.
For example, if a payment service provider experiences a data breach, they must quickly identify, contain, notify affected parties, and report the incident to regulatory bodies.
III. Digital Operational Resilience Testing
DORA legislation requires regular digital operational resilience testing to ensure financial entities can withstand and recover from ICT disruptions. Such a digital finance strategy involves:
- Conducting penetration tests to identify and fix vulnerabilities.
- Running disaster recovery drills to ensure systems can be restored after an incident.
- Testing backup systems to confirm data integrity and availability.
For example, an insurance company might simulate a ransomware attack to test its ability to restore data from backups and maintain operations without significant downtime.
IV. ICT Third-party Risk Management
Given the reliance on external ICT service providers, DORA emphasizes the need for stringent third-party risk management when offering digital services. As a result, financial entities must:
- Perform thorough due diligence on ICT service providers.
- Ensure contracts include provisions for security and resilience.
- Continuously monitor third-party performance and risks.
For example, a hedge fund working with a cloud service provider would regularly audit the provider’s security practices and have clear terms in the contract regarding incident response and data protection.
V. Information Sharing On Cyber Threats
DORA encourages financial entities to share information about cyber threats and vulnerabilities to enhance collective security. This includes:
- Participation in information-sharing networks and forums.
- Collaborating with other financial entities to identify and mitigate threats.
- Sharing anonymized incident data to help others strengthen their defenses.
For example, a consortium of banks might share details about a new phishing attack they encountered, allowing others to update their defenses accordingly.
Financial institutions can significantly enhance their ICT risk management, incident response, resilience testing, third-party risk management, and information-sharing capabilities by adhering to the key pillars above. Ultimately, these comprehensive measures ensure robust operational resilience, safeguarding against various ICT-related disruptions and threats.
Central Data Pain Points In Achieving DORA Compliance
As financial entities strive to meet the January 2025 compliance deadline, they encounter numerous data-related challenges. These challenges span across the key pillars explored earlier and are vital in the race to comply with DORA. Understanding and addressing these pain points is essential for achieving compliance and safeguarding against ICT-related disruptions. Let’s look at the ins and outs of central data pain points in achieving DORA compliance and setting the foundation for the secure digital transformation.
1. ICT Risk Management
As indicated, ICT risk management is a key part of DORA compliance. It requires financial institutions to find, judge, and lessen risks from their ICT systems. Yet, when doing so, financial entities face some major obstacles.
1. 1. Identifying and assessing ICT risks
Identifying and assessing ICT risks is a fundamental requirement of DORA. But, it presents significant challenges. Financial institutions must conduct thorough risk assessments to uncover all potential vulnerabilities within their ICT systems.
- Mapping the entire ICT ecosystem. Financial entities must map their entire ICT ecosystem, which includes hardware, software, networks, and data repositories. This comprehensive mapping is essential to identify all potential entry points for cyber threats.
- Assessing risk across various domains. Risks must be assessed across various domains, such as data integrity, availability, and confidentiality. Each domain has unique vulnerabilities and requires tailored assessment methods.
Thoroughly identifying and assessing ICT risks helps financial institutions. It lets them proactively address potential weaknesses. This forms the foundation for robust ICT risk management.
1. 2. Impact of evolving cyber threats and technological advancements
The rapid evolution of cyber threats and technological advancements adds another layer of complexity to risk identification and assessment. As a part of this pain point, one should focus on these aspects:
- Stay updated with emerging threats. Cyber threats continuously evolve, with new types of malware, phishing techniques, and attack vectors emerging regularly. Keeping up with these developments is essential for accurate risk assessment.
- Adapt to technological changes. As financial institutions adopt new technologies such as cloud computing, AI, and blockchain, they introduce new potential vulnerabilities. Each technological advancement requires its own set of security measures and risk assessments.
Keeping pace with evolving cyber threats and new technology is critical. It is key for accurate risk assessment and strong cybersecurity.
1. 3. Implementing risk management frameworks
Implementing new ICT risk management frameworks that comply with DORA can be challenging, especially when integrating them with existing systems. In this matter, financial entities face several difficulties:
- Legacy systems. Many financial institutions rely on legacy systems that must be designed with modern cybersecurity requirements in mind. Integrating new frameworks with these outdated systems can be complex and costly.
- Operational disruptions. Updating or replacing existing systems to accommodate new risk management frameworks can cause operational disruptions. This is particularly problematic for institutions that provide 24/7 financial services.
Doing new risk management requires planning. One must consider old systems and potential disruptions. As an outcome, the process takes more time and relies on additional resources.
Managing ICT risks under DORA presents financial entities with significant challenges. These tasks require substantial effort and resources, from identifying and assessing a broad spectrum of risks to integrating new frameworks with existing systems.
2. Incident Management And Reporting
Incident management and reporting are crucial components of DORA compliance. Financial institutions must establish robust systems to detect, report, and respond to ICT-related incidents promptly and effectively. Here, let’s explore the challenges of building these systems.
2. 1. Establishing robust incident reporting systems
One of the primary requirements of DORA is the timely and accurate reporting of ICT-related incidents. In a nutshell, it must these aspects should be in play:
- Rapid detection. Financial entities must quickly identify incidents to minimize damage and facilitate prompt reporting. This requires advanced monitoring tools and trained personnel.
- Accurate documentation. Detailed documentation of each incident is essential, including the nature of the incident, its impact, and the response actions taken. Accurate records help in compliance audits and future incident analysis.
Robust incident reporting systems let banks respond quickly to incidents. The speed of response often depends on the quality of detection and precision of documentation.
2. 2. Challenges in real-time threat detection and reporting
Detecting threats in real time and reporting them promptly is not a small feat. Naturally, it comes with several key pain points:
- A high volume of alerts. Financial institutions often receive a high volume of security alerts, many of which may be false positives. Sifting through these alerts to identify genuine threats can be time-consuming and resource-intensive.
- Coordination across teams. Effective incident reporting requires seamless coordination between different departments, such as IT, security, and compliance. Ensuring that all relevant information is communicated promptly and accurately can be challenging.
- Incident classification and prioritization. Incidents must be classified and prioritized based on their criticality and according to approved Service Level Agreements (SLAs). This ensures that the most severe threats are addressed first, minimizing potential damage.
Managing incident reporting and response under DORA presents significant challenges for financial institutions. These tasks require substantial effort and coordination, from establishing systems for timely and accurate reporting to coordinating across various teams for faster incident response.
3. Resilience Testing
Digital operational resilience testing is essential for ensuring financial institutions can withstand and recover from ICT-related disruptions.
3. 1. Importance of regular and comprehensive testing
Regular and comprehensive resilience testing is crucial for maintaining a robust security posture. The overall process must include these activities:
- Identifying vulnerabilities. Regular testing helps identify vulnerabilities in systems and processes before attackers can exploit them. It ensures that security measures are up-to-date and effective.
- Ensuring preparedness. Thorough testing readies banks to respond fast to real cyber-attacks. It cuts damage and disruptions.
Essentially, regular resilience testing ensures financial institutions can keep strong defenses. It also helps them respond fast to threats.
3. 2. Challenges in simulating realistic cyber-attack scenarios
To anticipate threats, companies often need to simulate incidents and cyberattacks. Yet, simulating realistic cyber-attack scenarios presents several challenges.
- Complexity of attacks. Cyber-attacks are becoming increasingly sophisticated, making it difficult to create realistic simulations that accurately reflect potential threats.
- Resource intensity. Developing and executing realistic attack simulations requires significant resources, including skilled personnel, advanced tools, and time.
Addressing the complexity and resource intensity of simulating realistic cyber-attacks is crucial for effective resilience testing.
3. 3. Balancing between thorough testing and operational disruptions
A key pain point is balancing thorough testing and minimizing operational disruptions. In such a context, the
- Schedule tests strategically. Planned and scheduled resilience tests during periods of low operational activity to minimize impact on daily operations.
- Use advanced tools. Employ advanced testing tools that simulate attacks with minimal disruption to live systems, ensuring thorough testing without compromising service availability.
Digital operational resilience testing is essential for ensuring DORA compliance and maintaining robust cybersecurity defenses. While conducting regular and comprehensive tests, financial institutions must navigate challenges such as simulating realistic cyber-attacks and balancing thorough testing with operational continuity.
4. Third-Party Risk Management
With DORA, financial institutions must ensure that their ICT service providers meet stringent security and resilience standards. Doing that can be a challenging task in itself. Here is why:
4. 1. Thorough due diligence and risk assessment
Conducting thorough due diligence and risk assessments of third-party ICT providers is vital to ensure they meet required security standards.
- Comprehensive assessments: Evaluating third-party providers’ security practices, financial stability, and compliance history to identify potential risks.
- Risk mitigation plans: Developing risk mitigation plans based on assessment findings to address identified vulnerabilities.
Thorough due diligence and risk assessments help third-party providers meet security standards and mitigate potential risks.
4. 2. Challenges in managing relationships with multiple third-party providers
Managing relationships with multiple third-party providers can be complex and resource-intensive. It definitely requires more attention and resources.
- Coordination and oversight. Ensuring consistent security standards and compliance across all providers requires significant coordination and oversight.
- Resource allocation. Allocating sufficient resources to monitor and manage multiple third-party relationships can strain an institution’s capabilities, especially for smaller organizations.
Effective coordination and resource allocation are essential for managing multiple third-party provider relationships. Otherwise, one can face a situation when DORA noncompliance of a third-party provider affects everyone involved. Overall, effective third-party risk management is essential for maintaining compliance with DORA and ensuring the security and resilience of financial institutions.
5. Information Sharing On Cyber Threats
Information sharing is a key component of DORA compliance. Financial institutions must collaborate to enhance collective security while balancing data privacy needs.
5. 1. Establishing secure information-sharing channels
Collaborative cybersecurity efforts are crucial for staying ahead of emerging threats. This involves:
- Threat intelligence sharing. Sharing threat intelligence with other financial institutions to collectively identify and mitigate emerging threats.
- Industry collaboration. Participating in industry forums and networks to exchange information on best practices and threat landscapes.
Establishing secure information-sharing channels enables financial institutions to stay ahead of emerging threats and enhance collective security.
- 2. Overcoming barriers to secure and efficient information sharing
Several barriers can hinder secure and efficient information sharing, including:
- Data sensitivity. Concerns about the sensitivity of shared information and potential exposure of vulnerabilities.
- Trust issues. Building trust among institutions ensures that shared information is used responsibly and securely.
Addressing data sensitivity and building trust is essential for effective and secure information sharing. Financial institutions can collaborate effectively while safeguarding data privacy by establishing secure information-sharing channels and implementing robust data protection measures.
Nine Strategies For Overcoming Data Pain Points In DORA Compliance
After reviewing the key data pain points, it is time to look at the brighter side. Overcoming the data pain points in achieving DORA compliance requires implementing effective strategies across various aspects of ICT risk management, incident response, resilience testing, third-party risk management, and information sharing. Let’s outline practical approaches to enhance these areas and ensure robust compliance with DORA.
Strategy 1. Enhancing Risk Management Practices
A comprehensive ICT risk management framework is essential for identifying, assessing, and mitigating risks. Developing a holistic approach that covers all aspects of ICT risk, including cyber threats, system failures, and data breaches, is crucial.
This framework should integrate seamlessly with existing risk management processes to be effective. Continuous improvement is also vital, which means regularly updating the framework to address new threats and vulnerabilities as they emerge. A well-rounded and continuously improving ICT risk management framework is crucial for maintaining robust security.
Strategy 2. Improving Incident Management Capabilities
Effective incident management requires well-defined response teams and protocols. This involves forming dedicated incident response teams with clearly defined roles and responsibilities.
Developing standardized protocols for different incidents also ensures a coordinated and effective response. Clear roles and standardized protocols enhance the efficiency and effectiveness of incident management.
Strategy 3. Leveraging Automation For Faster Incident Detection And Reporting
Automation can significantly enhance the speed and efficiency of incident detection and reporting. Deploying automated systems to monitor for signs of incidents and trigger alerts continuously is essential.
Furthermore, using automated tools to generate and submit incident reports to regulatory authorities quickly and accurately streamlines the reporting process. Here are some of the instruments to consider:
- Splunk. For real-time monitoring and analysis of security data.
- LogRhythm. For automated threat detection and response.
- Rapid7 InsightIDR. For continuous monitoring and incident detection.
- AlienVault OSSIM. Open-source SIEM for threat detection and response.
- McAfee ESM. For enterprise security management and incident response.
- Azure Sentinel. Microsoft’s cloud-native SIEM tool.
Automation improves incident detection and reporting speed and accuracy, enhancing overall incident management.
Strategy 4. Strengthening Resilience Testing Programs
Frequent and varied resilience tests are crucial for ensuring operational robustness. Scheduling regular resilience tests, including penetration testing, disaster recovery drills, and tabletop exercises, is vital.
Test against many scenarios. Ensure preparedness for different disruptions. Regular and varied testing offers comprehensive preparedness and identifies potential vulnerabilities.
Strategy 5. Integrating Test Findings Into Operational Improvements
Integrating findings from resilience tests into operational improvements is essential for continuous enhancement. Analyze test results to identify weaknesses and areas for improvement to get actionable insights.
Based on these findings, implement necessary changes to policies, procedures, and technologies. Using test results to inform operational improvements provides continuous enhancement of security measures.
Strategy 6. Optimizing Third-party Risk Management
Effective third-party risk management starts with rigorous vetting and continuous monitoring. Conducting thorough due diligence before engaging third-party providers ensures they meet security standards.
Monitoring third-party performance and compliance through regular audits and assessments is also crucial. Rigorous vetting and continuous monitoring are key to managing third-party risks effectively.
Strategy 7. Building Strong Contractual Agreements With Clear Risk Management Clauses
Strong contractual agreements are essential for managing third-party risks. Include specific clauses defining security requirements, performance metrics, and incident response protocols in contracts with third-party providers.
In addition, establishing clear exit strategies ensures a smooth transition if a third-party provider fails to meet security standards. Clear and detailed contractual agreements help mitigate third-party risks and ensure smooth transitions if needed.
Strategy 8. Facilitating Effective Information Sharing
Secure platforms for information sharing enhance collective cybersecurity efforts. Developing or using existing secure platforms for exchanging threat intelligence and best practices is fundamental. Implementing robust access controls ensures that only authorized personnel can share and access information.
Strategy 9. Promoting A Culture Of Transparency And Collaboration In Cybersecurity
Promoting a culture of transparency and collaboration is vital for effective information sharing. Encourage all stakeholders to participate actively in information-sharing initiatives to foster a collaborative environment. Establish trust among institutions to ensure shared information is used responsibly and securely. A culture of transparency and trust equals effective collaboration in cybersecurity.
Financial institutions can address data challenges and meet DORA compliance by following these strategies. This includes enhancing risk management practices, improving incident response capabilities, strengthening resilience testing programs, optimizing third-party risk management, and facilitating effective information sharing to build a more resilient and secure operational framework.
Conclusion
Remember, being proactive about following the rules and preparing for potential issues to benefit from DORA is important. Make sure to comply with regulations early and thoroughly to improve overall security. Keep up with regular reviews and updates to maintain operational resilience. Taking a proactive approach will help institutions better prepare for threats and minimize the impact of disruptions in ICT.
Understanding and addressing key data pain points in achieving DORA compliance can help build a resilient and secure operational framework. Embracing advanced technologies, fostering transparency and collaboration, and prioritizing continuous learning will be crucial for navigating future regulatory developments.
For expert assistance in achieving DORA compliance, contact Avenga. Our team can help you navigate the complexities and ensure your institution is fully prepared.



