How to build a security-first compliance framework for financial services

February 26, 2026 8 min read
As the finance industry continues to undergo a rapid digital transformation, data security in financial services has become a defining competitive factor – not just a technical requirement. With the fintech category expected to grow to $1,126 billion by 2032 at a steady 16.2% CAGR, the pressure to protect sensitive data is growing. Financial institutions and fintech innovators have a dual responsibility to introduce new products and features that comply with rules and regulations. Every new feature or integration must ensure that security standards are consistently adhered to at every step. A strong data security financial services strategy is not optional—but a core principle of trust, resilience, and regulatory preparedness. For any finance software development company, employing a security-first approach to compliance means embedding protection and governance into every layer of technology.
This article explains what a security-first compliance framework is, its importance, and how to build one that protects both your business and your customers.
Key insights from this guide
- The financial services industry is facing rising data breaches and rapidly changing regulatory expectations.
- A security-first compliance framework builds protection, monitoring, and governance into all layers of technology and elsewhere.
- Structured, phased approach strengthen data defenses and reduce risk without slowing innovation.
- By investing proactively in security, organizations can turn compliance into a strategic advantage – not just a mandatory task.
Why a security-first mindset matters more than ever
Recent research indicates an alarming finding: 18.4% of fintech organizations have reported breaches in the public domain, and 28.2% of these companies have reported more than one breach. Even more alarming, 46.4% reported the lowest score in Application Security, which exposed a lack of diligence associated with core systems, including Application Security and DNS Health.
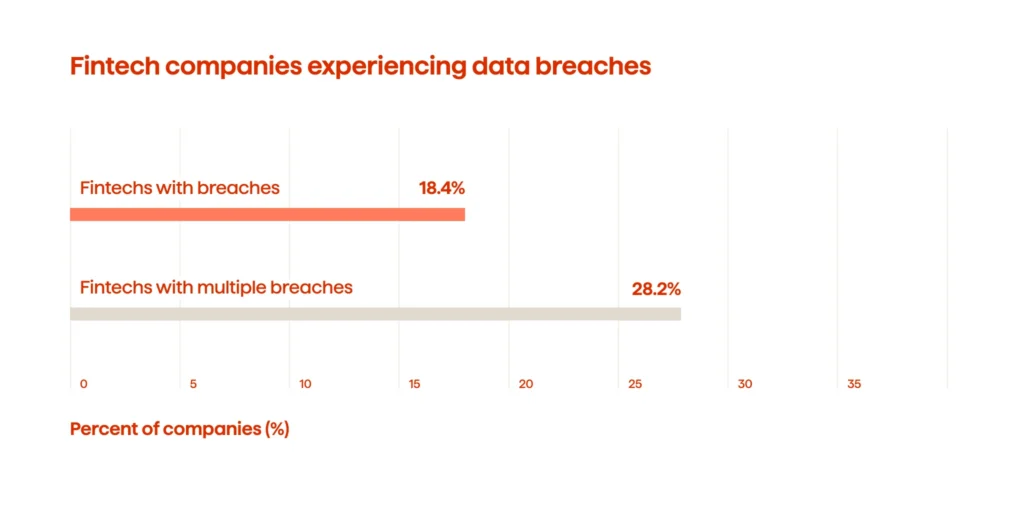
This data reinforces the case for a security-first approach to protecting data in the financial services space. As digital finance ecosystems continue to expand, the volume of sensitive data associated with financial services — including transactions, identities, and financial records—will also continue to grow. The absence of robust data security in financial services organizations risks not only financial loss but also regulatory penalties and, long-term damage to brand reputation and customer loyalty.
There are three main reasons why security-first is non-negotiable:
1. Cyberthreats are becoming more complex and harder to detect. Interconnected APIs, third-party integrations, and outdated infrastructure are increasingly being used in modern attacks. By embedding protection into architecture and development standards early, some of this risk can be eliminated before exploitation occurs..
2. Increased regulatory pressure and reputational risk. New standards such as DORA, PCI DSS, and ISO 27001 all require ongoing monitoring and proof of resilience. Security has become the foundation of compliance – not just a checkbox.
3. Customer trust is currency. For any financial institution, trust is a key to retention. Effective data security practices in the financial services industry provide customers with the assurance that their data will be handled with integrity, thereby fostering trust and loyalty.
Achieve unparalleled growth with Avenga’s tailored digital banking solutions.
Understanding what a security-first compliance framework really is
A security-first compliance framework is both a way of thinking and a framework that integrates detailed data security into financial services at every reasonable point where risks, regulations, and technology overlap. In other words, it turns security for financial services into a starting point rather than an afterthought.
What it looks like in practice
Consider a financial services company introducing a new digital wallet offering. Instead of merely checking boxes on regulatory requirements (such as AML or KYC), the company begins by mapping how data flows, where it’s stored, how access happens, and what threats might be present. It then has a security baseline. Compliance controls, which include audit logs, policy rules, and reporting, are applied on top, not under. For example, the financial firm may utilize ISO 27001 (an information security management standard) in conjunction with the EU DORA regulation to enhance operational resilience.
Here’s a table summarising essential building blocks:
| Component | What it ensures | Example in action |
|---|---|---|
| Risk-based controls | Priorities the highest threats | Continuous vulnerability scanning of payment APIs |
| Governance and culture | Everyone from the board to the engineer shares ownership of compliance | Mandatory annual training + real-time phishing simulation |
| Technical safeguards | Encryption, least-privilege IAM, secure SDLC | Crypto-at-rest for wallet data; devs use secure code libraries |
| Monitoring and response | Detect, investigate, recover | 24/7 logs feeding SIEM, quick incident playbooks |
| Audit and improvement | Framework evolves with business changes | Quarterly control reviews when product or region changes |
When data security in financial services is treated as business-critical and controls are built first, compliance becomes secondary; organizations turn regulatory compliance into a means to achieve a competitive advantage rather than a regulatory cost. A framework built this way will provide strength, regulatory alignment, and, most importantly, trust.
How to build a security-first compliance framework — step by step
A compliance program with a security-first framework is not created in one workshop. It is a program that encompasses governance, technology, and culture. Here is a practical implementation roadmap you can actually follow.
Step 1: Map your data and risk surface
Begin by obtaining a solid understanding of what you are protecting. Types of data (PII, payment data, trading data), where data resides, who can access the data, and how data flows between systems. This will serve as the foundation for data protection in financial services, outlining where to implement controls effectively to ensure robust data protection.
Deliverable: Data Flow Map, Risk Surface Inventory
Step 2: Align with regulations and internal policies
Provide a list of regulations or other applicable standards that apply to yourself (e.g., GDPR, PCI DSS, ISO 27001, local banking regulations). Map these regulations/standards to controls, for example: encryption, retention requirements, access/permission reviews, logging, and incident response. The focus here will not be on “compliance for the sake of compliance”, but compliance as it relates to absolute security for financial services.
Deliverable: Control Mapping Matrix, Gap analysis
Step 3: Execute multi-layer and risk-based controls
Implementing defense-in-depth controls throughout your infrastructure, application, and endpoint. Network segmentation, cloud configurations hardening, secure SDLC, strong IAM, MFA, and secrets management are all essential controls. Ensure that you prioritize controls and items based on risk (e.g., processing payments, validating identity data, and transactions with higher values).
Deliverable: Risk-Prioritized Control Implementation Plan
Step 4: Use monitoring that creates a data product
Utilize data analytics services to transform raw logs into actionable insights. Aggregate events from applications, APIs, database systems, and identity providers into a SIEM or data lake. Build dashboards that will display anomalous logins, user policy violations, or unusual transactions. Position this directly as value: continuous monitoring reduces detection time, supports compliance reporting, and prevents fraud.
Deliverable: Threat & Compliance Alerting and Analytics (Alerts, Reports, Dashboards)
Step 5: Operationalize incident response and playbooks
Develop a series of procedures that outline the following steps when a suspicion of an issue arises, including who to inform, how the team determines the next course of action, and what will be communicated to consumers and regulators once the issue is assessed. Build playbooks to consider potential scenarios (e.g., phishing, credential theft, API exploitation), and rehearse them through tabletop exercises.
Deliverable: Operations Run book + Communication Matrix
Step 6: Embed security into people and processes
If the security team is only aware of or understands the framework being implemented, the framework will not be practical. Consult and guide product, engineering, and operations teams on security practices, including secure coding, access hygiene, and best practices for leveraging the access tools implemented. Integrate security checklists into change management and release pipeline processes, ensuring that security is a factor integrated into the continual process and all phases of the application development life cycle, to help secure the application.
Deliverable: Role-based Security Training
Step 7: Continuously review, test, and improve
Schedule regular audits, pen tests, or policy reviews. Incorporate learnings and analytics from incidents into your framework, enabling a continuous and natural evolution of the framework’s effectiveness.
Deliverable: Regular (Monthly, Quarterly, Yearly Review Reports + Continuous Updates of the Framework
FAQs: Your top questions answered
1. What is a security-first compliance framework in financial services?
A security-first framework implements protection, governance, and monitoring throughout the entire product development life cycle, as well as operational controls. It also establishes trust and ongoing protection of data in financial services.
2. How do security-first organizations improve regulatory compliance?
Businesses that prioritize security have regulations that are in line with objective, quantifiable, and auditable technology controls, including logging, IAM, encryption, and retention policies.
3. Why is constant monitoring critical?
Because threats evolve daily, continuous monitoring takes raw logs and transforms them into actionable intelligence, providing visibility into suspicious activity sooner and enabling a rapid response. This provides an essential requirement for the reasonable and proper protection of your data in the financial services sector.
4. How often should the security-first framework be reviewed?
Quarterly would be ideal; however, it could be after any changes in infrastructure, products, or regulations have been implemented. Regular reviews reduce the likelihood that one or more of your controls are ineffective in addressing your risk or are no longer capable of meeting a compliance requirement.
Turning compliance into lasting trust
In an industry of promises, feeling assured in your security for financial services is a benefit. A security-first compliance ecosystem transforms regulation from a cost center into a competitive advantage, providing enhanced resilience, faster innovation, and more protection for trust.
The final insight is straightforward: trust is not explicitly stated in modern finance. It is engineered. Through rigorous data protection in financial services, you create a system in which security is the strongest offering you have to offer.Contact Avenga, your trusted technology partner, to learn more about our services.